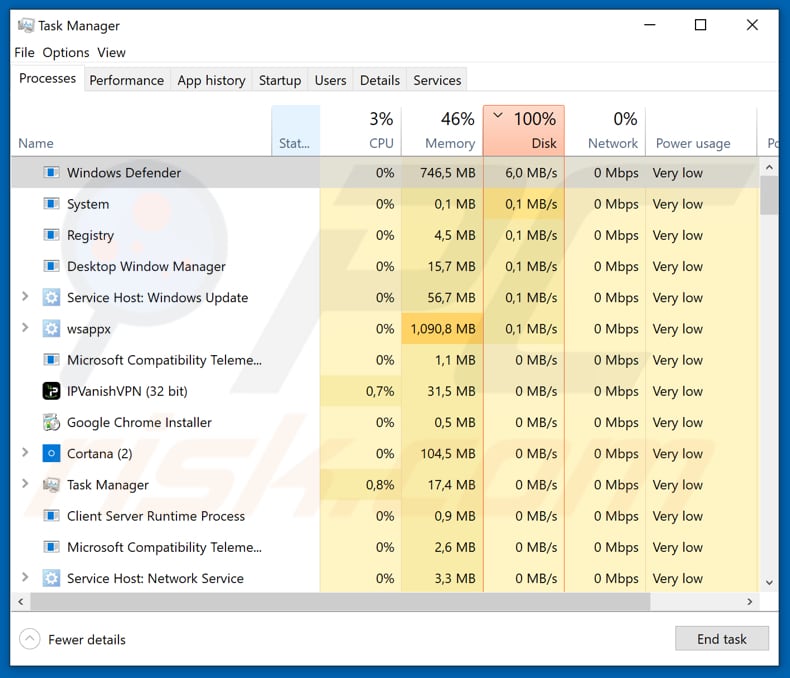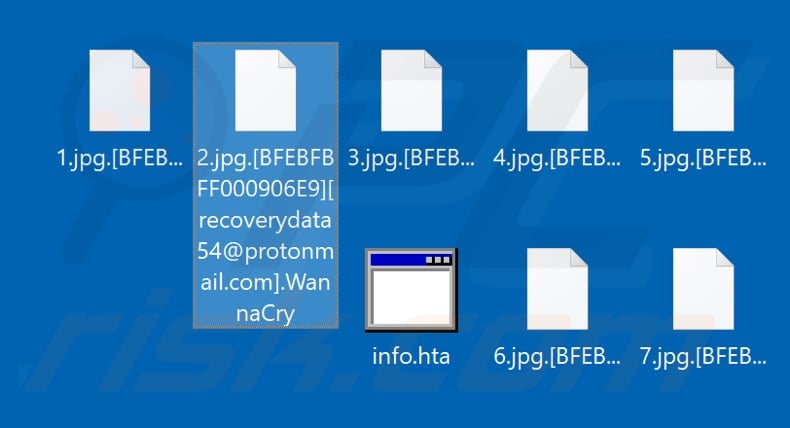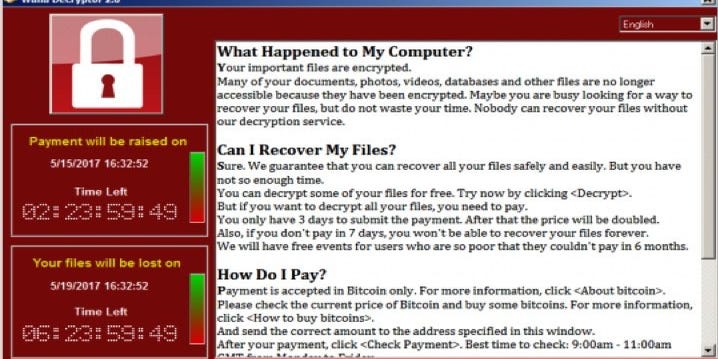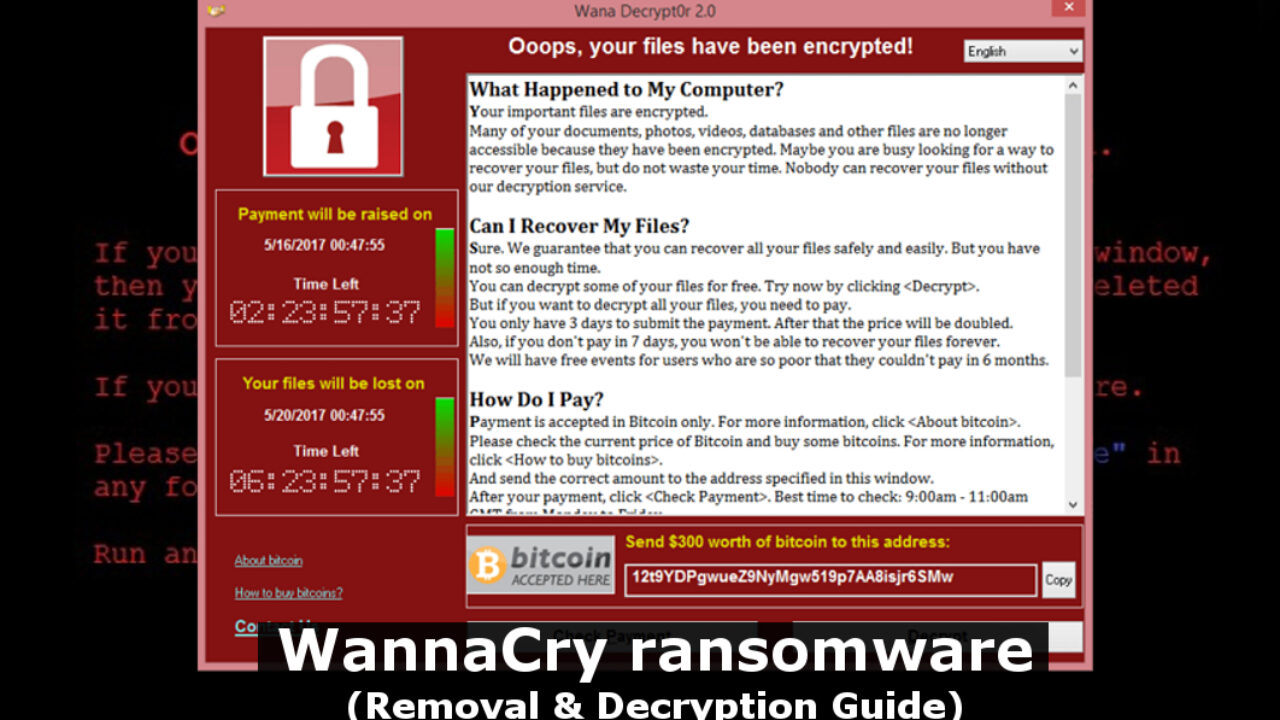
Ransomware deployment methods and analysis: views from a predictive model and human responses | Crime Science | Full Text

Cyber-Physical Attacks and the Value of Healthcare Data: Facing an Era of Cyber Extortion and Organised Crime | SpringerLink